WordPress Vulnerability Report: September 2021, Part 5
Vulnerable plugins and themes are the #1 reason WordPress websites get hacked. The weekly WordPress Vulnerability Report powered by WPScan covers recent WordPress plugin, theme, and core vulnerabilities, and what to do if you run one of the vulnerable plugins or themes on your website. Each vulnerability will have a severity rating of Low, Medium, High, or Critical.

Vulnerable plugins and themes are the #1 reason WordPress websites get hacked. The weekly WordPress Vulnerability Report powered by WPScan covers recent WordPress plugin, theme, and core vulnerabilities, and what to do if you run one of the vulnerable plugins or themes on your website.
Each vulnerability will have a severity rating of Low, Medium, High, or Critical. Responsible disclosure and reporting of vulnerabilities is an integral part of keeping the WordPress community safe.
As one of the largest WordPress Vulnerability Reports to date, please share this post with your friends to help get the word out and make WordPress safer for everyone.
Get SolidWP tips direct in your inbox
Sign up
Get started with confidence — risk free, guaranteed
WordPress Core Vulnerabilities
Several WordPress core security issues were disclosed and fixed. WordPress 5.8.1 was released as a security and maintenance release. As a best practice, always be sure to run the latest version of WordPress core!
WordPress Plugin Vulnerabilities
In this section, the latest WordPress plugin vulnerabilities have been disclosed. Each plugin listing includes the type of vulnerability, the version number if patched, and the severity rating.
1. Comments – wpDiscuz
Plugin: Comments – wpDiscuz
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 7.3.2
Severity Score: Low
2. Page Generator

Plugin: Page Generator
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 1.5.9
Severity Score: High
3. WordPress to Hootsuite

Plugin: WordPress to Hootsuite
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 1.3.9
Severity Score: High
4. WordPress to Buffer

Plugin: WordPress to Buffer
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 3.7.5
Severity Score: High
5. Gutenberg PDF Viewer Block
Plugin: Gutenberg PDF Viewer Block
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: 1.0.1
Severity Score: Medium
6. YITH WooCommerce Product Add-Ons
Plugin: YITH WooCommerce Product Add-Ons
Vulnerability: Authenticated Local File Inclusion
Patched in Version: 2.1.0
Severity Score: Medium
Plugin: YITH WooCommerce Product Add-Ons
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 2.1.0
Severity Score: High
7. To Top
Plugin: To Top
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 2.3
Severity Score: Medium
7. Header Enhancement
Plugin: Header Enhancement
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.5
Severity Score: Medium
8. Generate Child Theme

Plugin: Generate Child Theme
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.6
Severity Score: Medium
9. Essential Content Types

Plugin: Essential Content Types
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.9
Severity Score: Medium
9. Catch Web Tools
Plugin: Catch Web Tools
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 2.7
Severity Score: Medium
10. Essential Widgets
Plugin: Software License Manager
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.9
Severity Score: Medium
11. Catch Under Construction

Plugin: Catch Under Construction
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.4
Severity Score: Medium
12. Catch Themes Demo Import
Plugin: Catch Themes Demo Import
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.6
Severity Score: Medium
13. Catch Sticky Menu
Plugin: Catch Sticky Menu
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.7
Severity Score: Medium
14. Catch Scroll Progress Bar
Plugin: Catch Scroll Progress Bar
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.6
Severity Score: Medium
15. Social Gallery and Widget

Plugin: Social Gallery and Widget
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 2.3
Severity Score: Medium
16. Catch Infinite Scroll

Plugin: Catch Infinite Scroll
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.9
Severity Score: Medium
17. Catch Import Export
Plugin: Catch Import Export
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.9
Severity Score: Medium
18. Catch Gallery

Plugin: Catch Gallery
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.7
Severity Score: Medium
19. Catch Duplicate Switcher
Plugin: Catch Duplicate Switcher
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.6
Severity Score: Medium
20. Catch Breadcrumb
Plugin: Catch Breadcrumb
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 1.7
Severity Score: Medium
21. Catch IDs
Plugin: Catch IDs
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 2.4
Severity Score: Medium
22. Tutor LMS
Plugin: Tutor LMS
Vulnerability: Multiple Admin+ Stored Cross-Site Scripting
Patched in Version: 1.9.9
Severity Score: Low
23. WP Import Export Lite

Plugin: WP Import Export Lite
Vulnerability: Subscriber+ Extensions Update
Patched in Version: 3.9.5
Severity Score: Medium
Plugin: WP Import Export Lite
Vulnerability: Subscriber+ Arbitrary Blog Options Update
Patched in Version: 3.9.5
Severity Score: Medium
24. One User Avatar
Plugin: One User Avatar
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: 2.3.7
Severity Score: Medium
Plugin: One User Avatar
Vulnerability: Avatar Update via CSRF
Patched in Version: 2.3.7
Severity Score: Medium
25. Scroll Baner
Plugin: Scroll Baner
Vulnerability: CSRF to RCE
Patched in Version: no known fix
Severity Score: Critical
26. WP Ticket

Plugin: WP Ticket
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 5.10.4
Severity Score: Low
27. GamePress
Plugin: GamePress
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: no known fix
Severity Score: High
28. Wechat Reward
Plugin: Wechat Reward
Vulnerability: CSRF to Stored Cross-Site Scripting
Patched in Version: no known fix
Severity Score: High
29. Sociable
Plugin: Sociable
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: no known fix
Severity Score: Low
30. BetterDocs
Plugin: BetterDocs
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 1.9.2
Severity Score: High
31. Multiple WooCommerce Add-Ons – multiple plugins
Plugin: Product Filter for WooCommerce
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 8.2.0
Severity Score: High
Plugin: improved-variable-product-attributes
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 5.3.0
Severity Score: High
Plugin: improved-sale-badges
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 4.4.0
Severity Score: High
Plugin: share-print-pdf-woocommerce
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 2.8.0
Severity Score: High
Plugin: product-loops
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 1.7.0
Severity Score: High
Plugin: XforWooCommerce
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 1.7.0
Severity Score: High
Plugin: package-quantity-xforwc
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 1.2.0
Severity Score: High
Plugin: price-commander-xforwc
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 1.3.0
Severity Score: High
Plugin: spam-control-xforwc
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 1.5.0
Severity Score: High
Plugin: add-tabs-xforwc
Vulnerability: Low Priv Arbitrary Blog Options Update/Access/Deletion & Plugin’s Settings Update/Export/Import
Patched in Version: 1.5.0
Severity Score: High
32. WP Cookie Choice
Plugin: WP Cookie Choice
Vulnerability: CSRF to Stored Cross-Site Scripting
Patched in Version: no known fix
Severity Score: High
33. Easy Twitter Feed
Plugin: Easy Twitter Feed
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: 1.2
Severity Score: Medium
34. Html5 Audio Player
Plugin: Html5 Audio Player
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: 2.1.3
Severity Score: Medium
35. Polo Video Gallery
Plugin: Polo Video Gallery
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Medium
36. StreamCast

Plugin: StreamCast
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: 2.1.1
Severity Score: Medium
37. PDF Light Viewer

Plugin: PDF Light Viewer
Vulnerability: Authenticated Command Injection
Patched in Version: 1.4.12
Severity Score: Low
38. MainWP Child Reports

Plugin: MainWP Child Reports
Vulnerability: Admin+ SQL Injection
Patched in Version: 2.0.8
Severity Score: Medium
39. LearnPress

Plugin: LearnPress
Vulnerability: Unauthorised Plugin’s Setting Change
Patched in Version: 4.1.3.1
Severity Score: Low
Plugin: LearnPress
Vulnerability: Multiple Admin+ Stored Cross-Site Scripting
Patched in Version: 4.1.3.1
Severity Score: Low
40. OptinMonster
Plugin: OptinMonster
Vulnerability: Reflected Cross-Site Scripting (XSS)
Patched in Version: 2.6.1
Severity Score: Medium
41. Frontend Uploader
Plugin: Frontend Uploader
Vulnerability: Unauthenticated Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Medium
42. Allow REL= and HTML in Author Bios
Plugin: Allow REL= and HTML in Author Bios – WordPress plugin | WordPress.org
Vulnerability: Author+ Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Medium
43. WP HTML Author Bio
Plugin: WP HTML Author Bio
Vulnerability: Author+ Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Medium
44. jQuery Reply to Comment
Plugin: jQuery Reply to Comment
Vulnerability: CSRF to Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: High
45. Video Gallery – Vimeo and YouTube Gallery
Plugin: Video Gallery – Vimeo and YouTube Gallery
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Low
46. Request a Quote

Plugin: Request a Quote
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 2.3.5
Severity Score: Low
47. St Daily Tip
Plugin: St Daily Tip
Vulnerability: CSRF to Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: High
48. Advance Search

Plugin: Advance Search
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 1.1.3
Severity Score: Medium
49. WP Mega Menu
Plugin: WP Mega Menu
Vulnerability: Subscriber+ Arbitrary Post Access
Patched in Version: 1.4.1
Severity Score: Medium
Plugin: WP Mega Menu
Vulnerability: Unauthenticated Arbitrary Post Access
Patched in Version: 1.4.0
Severity Score: High
50. Cherry Plugin
Plugin: Cherry Plugin
Vulnerability: Unauthenticated Arbitrary File Upload and Download
Patched in Version: 1.2.7
Severity Score: Critical
51. WP Job Manager
Plugin: WP Job Manager – WordPress plugin | WordPress.org
Vulnerability: Phar Deserialization
Patched in Version: 1.31.3
Severity Score:
Plugin: WP Job Manager – WordPress plugin | WordPress.org
Vulnerability: Unauthenticated Object Injection
Patched in Version: 1.29.3
Severity Score: Medium
Plugin: WP Job Manager – WordPress plugin | WordPress.org
Vulnerability: Unauthenticated Arbitrary File Upload
Patched in Version: 1.26.2
Severity Score: Critical
Plugin: WP Job Manager – WordPress plugin | WordPress.org
Vulnerability: Reflected Cross-Site Scripting (XSS)
Patched in Version: 1.23.8
Severity Score: High
52. WP Mobile Detector
Plugin: WP Mobile Detector
Vulnerability: Unauthenticated Arbitrary File Upload
Patched in Version: 3.6
Severity Score: Critical
53. Telefication
Plugin: Telefication
Vulnerability: Open Relay & Server-Side Request Forgery
Patched in Version: no known fix – plugin closed
Severity Score: Medium
54. Game Server Status
Plugin: Game Server Status
Vulnerability: Contributor+ SQL Injection
Patched in Version: no known fix – plugin closed
Severity Score: High
Plugin: Game Server Status
Vulnerability: Admin+ SQL Injection
Patched in Version: no known fix – plugin closed
Severity Score: Medium
Plugin: Game Server Status
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Low
55. Responsive WordPress Slider
Plugin: Responsive WordPress Slider
Vulnerability: Subscriber+ Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Critical
Plugin: Responsive WordPress Slider
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Critical
56. Fetch Tweets
Plugin: Fetch Tweets
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: High
57. WooCommerce

Plugin: WooCommerce
Vulnerability: Analytics Report Leaks
Patched in Version: 5.7.0
Severity Score: Medium
58. WooCommerce Admin

Plugin: WooCommerce Admin
Vulnerability: Analytics Report Leaks
Patched in Version: 2.6.0
Severity Score: Medium
59. YT Player

Plugin: YT Player
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: 1.4
Severity Score: Medium
60. Cookie Bar
Plugin: Cookie Bar
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: no known fix – plugin closed
Severity Score: Low
61. WP User Manager

Plugin: WP User Manager
Vulnerability: Arbitrary User Password Reset to Account Compromise
Patched in Version: 2.6.3
Severity Score: High
62. Easy Media Download

Plugin: Easy Media Download
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: 1.1.7
Severity Score: Medium
63. Ninja Forms
Plugin: Ninja Forms
Vulnerability: Unprotected REST-API to Sensitive Information Disclosure
Patched in Version: 3.5.8
Severity Score: Medium
Plugin: Ninja Forms
Vulnerability: Unprotected REST-API to Email Injection
Patched in Version: 3.5.8
Severity Score: Medium
Plugin: Ninja Forms
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 3.5.8.2
Severity Score: Low
64. 3DPrint Lite
Plugin: 3DPrint Lite
Vulnerability: Unauthenticated Arbitrary File Upload
Patched in Version: no known fix – plugin closed
Severity Score: Critical
65. iQ Block Country

Plugin: iQ Block Country
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 1.2.12
Severity Score: Low
66. WordPress Popular Posts
Plugin: WordPress Popular Posts
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 5.3.4
Severity Score: Low
67. Custom Dashboard & Login Page

Plugin: Custom Dashboard & Login Page
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 6.9.2
Severity Score: Low
68. Bug Library

Plugin: Bug Library
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 2.0.4
Severity Score: Medium
A Note on Responsible Disclosure
You might be wondering why a vulnerability would be disclosed if it gives hackers an exploit to attack. Well, it is very common for a security researcher to find and privately report the vulnerability to the software developer.
With responsible disclosure, the researcher’s initial report is made privately to the developers of the company that owns the software, but with an agreement that the full details will be published once a patch has been made available. For significant security vulnerabilities, there may be a slight delay in disclosing the vulnerability to give more people time to patch.
The security researcher may provide a deadline for the software developer to respond to the report or to provide a patch. If this deadline is not met, then the researcher may publicly disclose the vulnerability to put pressure on the developer to issue a patch.
Publicly disclosing a vulnerability and seemingly introducing a Zero-Day vulnerability–a type of vulnerability that has no patch and is being exploited in the wild– may seem counterproductive. But, it is the only leverage that a researcher has to pressure the developer to patch the vulnerability.
If a hacker were to discover the vulnerability, they could quietly use the Exploit and cause damage to the end-user(this is you), while the software developer remains content on leaving the vulnerability unpatched. Google’s Project Zero has similar guidelines when it comes to disclosing vulnerabilities. They publish the full details of the vulnerability after 90 days whether or not the vulnerability has been patched.
How to Protect Your WordPress Website From Vulnerable Plugins and Themes
As you can see from this report, lots of new WordPress plugin and theme vulnerabilities are disclosed each week. We know it can be difficult to stay on top of every reported vulnerability disclosure, so the iThemes Security Pro plugin makes it easy to make sure your site isn’t running a theme, plugin or WordPress core version with a known vulnerability.
1. Turn on the iThemes Security Pro Site Scanner
The iThemes Security Pro plugin’s Site Scanner scans for the #1 reason WordPress sites get hacked: outdated plugins and themes with known vulnerabilities. The Site Scanner checks your site for known vulnerabilities and automatically applies a patch if one is available.
To enable the Site Scan on new installs, navigate to the Site Check tab on the Features menu inside the plugin and click the toggle to enable the Site Scan.
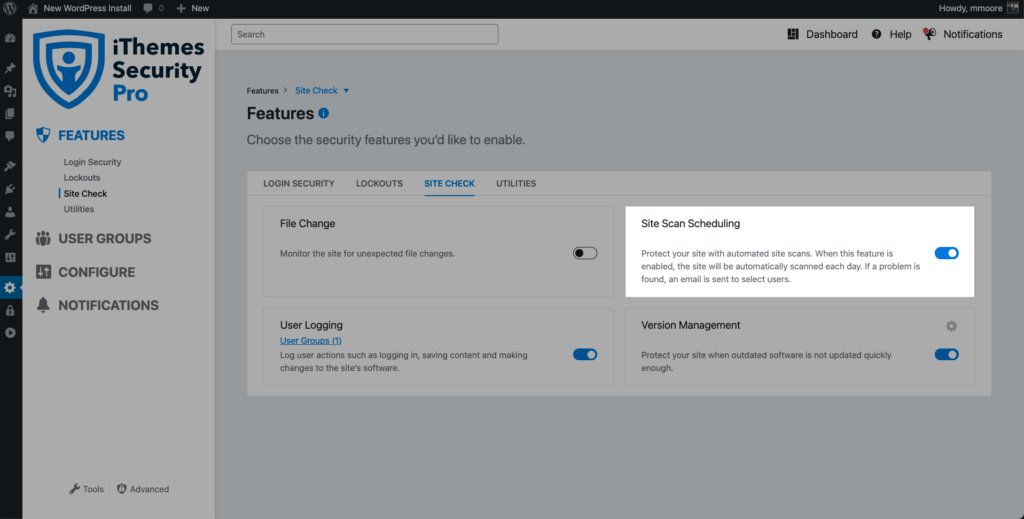
To trigger a manual Site Scan, click the Scan Now button on the Site Scan Security Dashboard card.
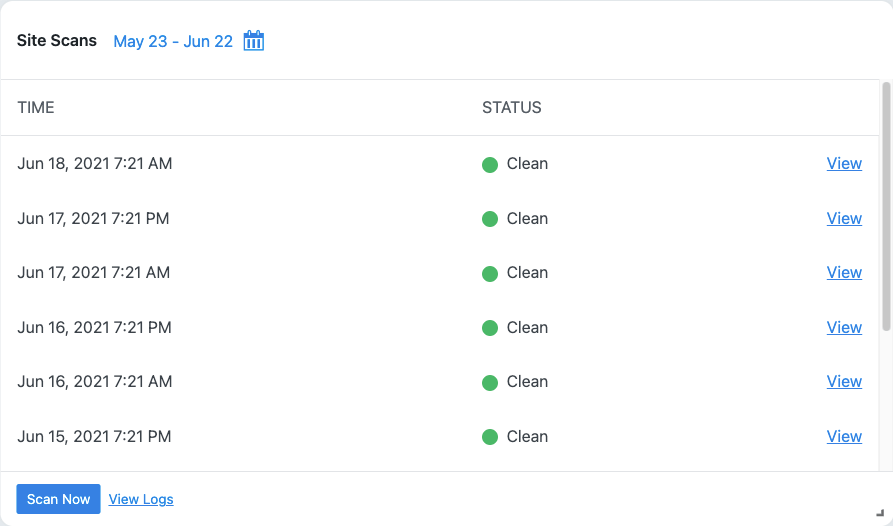
If the Site Scan detects a vulnerability, click the vulnerability link to view the details page.
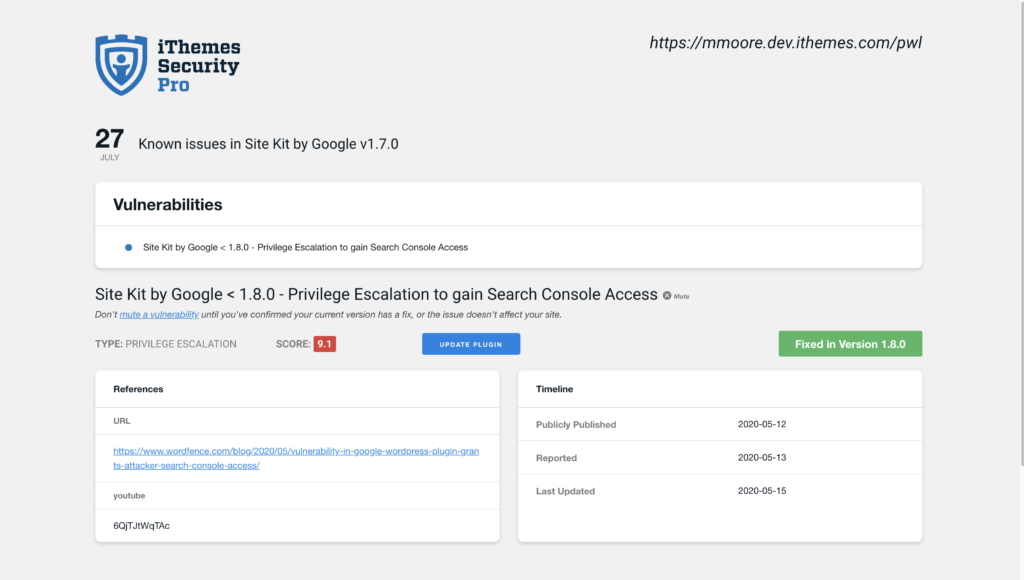
On the Site Scan vulnerability page, you will see if there is a fix available for the vulnerability. If there is a patch available, you can click the Update Plugin button to apply the fix on your website.
2. Turn on Version Management to Auto Update if Fixes Vulnerability
The Version Management feature in iThemes Security Pro integrates with the Site Scan to protect your site when outdated software is not updated quickly enough. Even the strongest security measures will fail if you are running vulnerable software on your website. These settings help protect your site with options to update to new versions automatically if a known vulnerability exists and a patch is available.
From the Settings page in iThemes Security Pro, navigate to the Features screen. Click the Site Check tab. From here, use the toggle to enable Version Management. Using the settings gear, you can configure even more settings, including how you want iThemes Security Pro to handle updates to WordPress, plugins, themes, and additional protection.
Make sure to select Auto Update if it Fixes a Vulnerability box so that iThemes Security Pro will automatically update a plugin or theme if it fixes a vulnerability that was found by the Site Scanner.
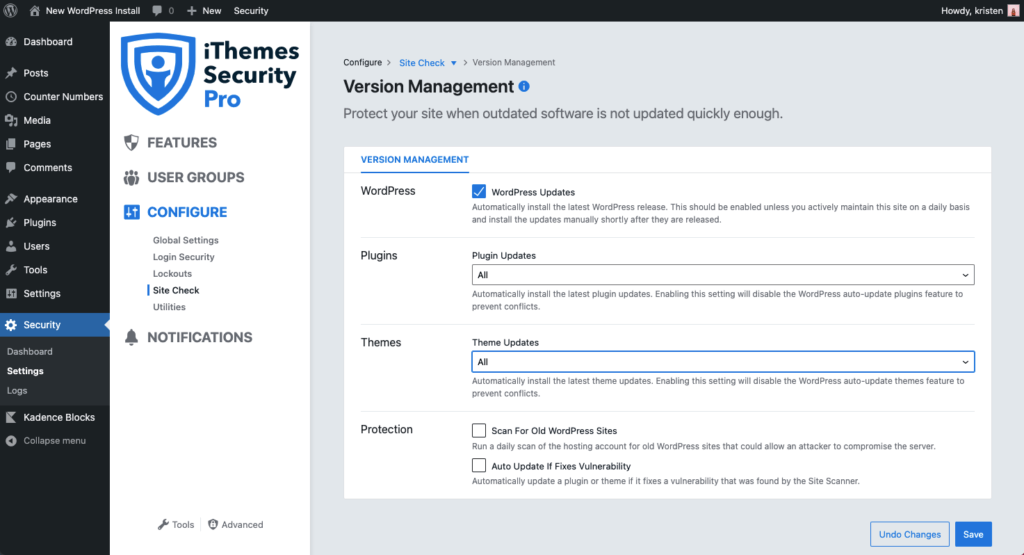
3. Get an Email Alert When iThemes Security Pro Finds a Known Vulnerability On Your Site
Once you’ve enabled Site Scan Scheduling, head to the Notification Center settings of the plugin. On this screen, scroll to the Site Scan Results section.
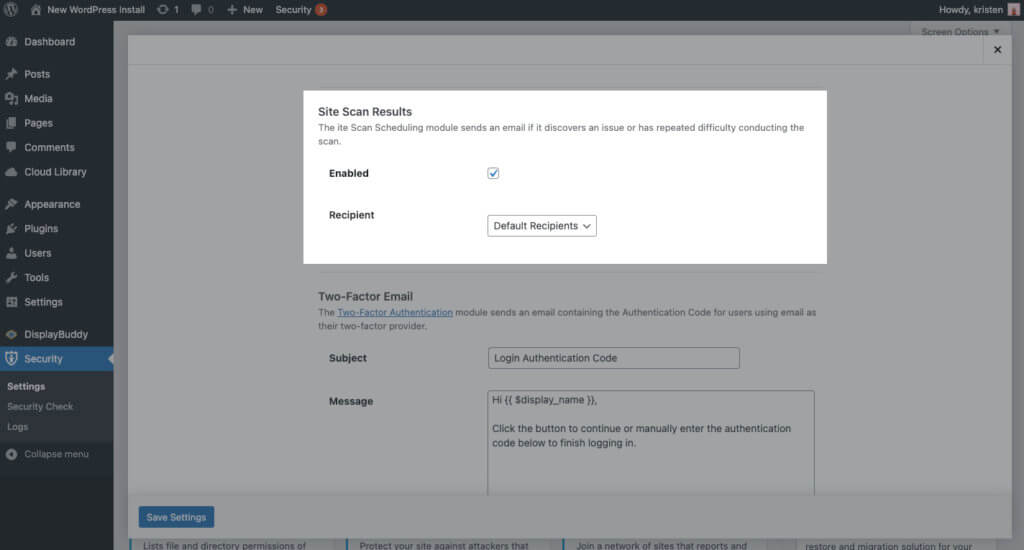
Click the box to enable the notification email and then click the Save Settings button.
Now, during any scheduled site scans, you’ll get an email if iThemes Security Pro discovers any known vulnerabilities. The email will look something like this.
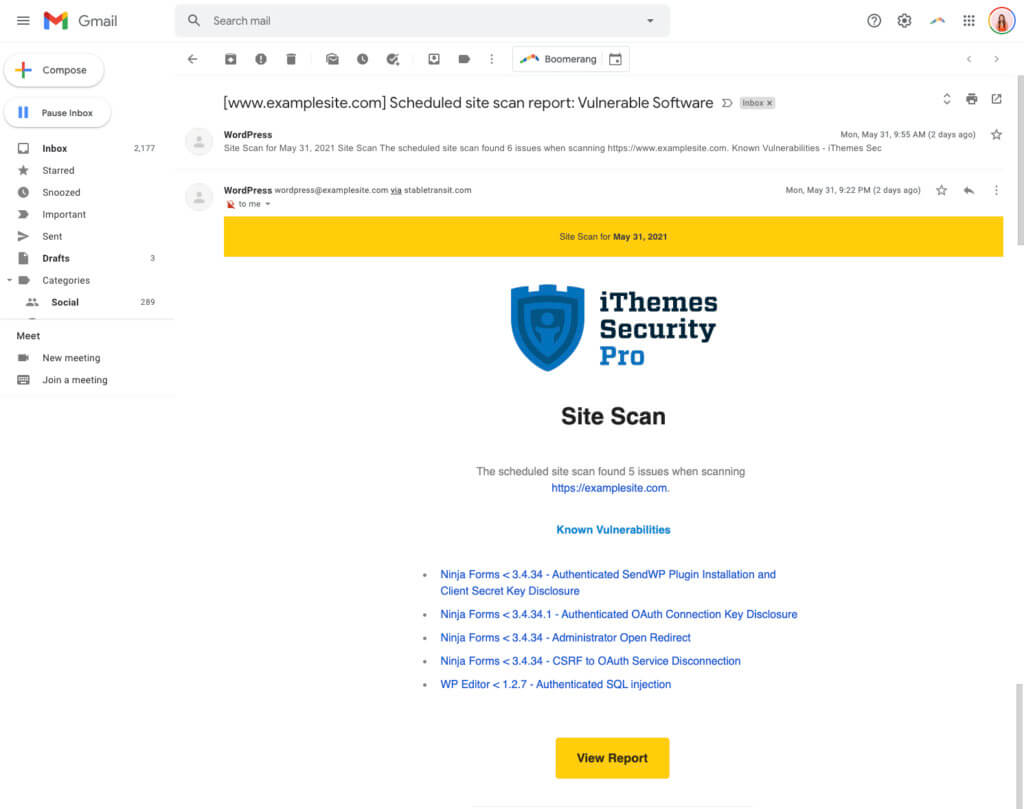
Get iThemes Security Pro and Rest a Little Easier Tonight
iThemes Security Pro, our WordPress security plugin, offers 50+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add extra layers of security to your website.
Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed