Introduction to Two Factor Authentication
Something you hear about often in relation to digital security today is two factor authentication (also referred to as 2FA or multi-factor authentication), and rightly so. Two factor authentication can dramatically increase security. What is Two Factor Authentication? There are three basic factors that can be used for authentication: Something you know (Maybe a password, secret, or PIN) Something you have (Your mobile phone or another device such as a key or fob) Something you are (Biometrics such as a retina or fingerprint) A classic username and password authentication system uses only one factor because both pieces of data are "something you know" (and generally a username is public information anyway, so it doesn't affect security).

What is Two Factor Authentication?
There are three basic factors that can be used for authentication:- Something you know (Maybe a password, secret, or PIN)
- Something you have (Your mobile phone or another device such as a key or fob)
- Something you are (Biometrics such as a retina or fingerprint)
What are the Benefits of Two Factor Authentication?
Two factor authentication should not take the place of a high quality, unique password; instead it should augment it. Two factor authentication actually works kind of like a safety deposit box at a bank. You have a key, but you also need to show identification. You can’t get into the box without both. There was an incident a while ago where a guy named Mat was hacked via social engineering. The strength of his password really never came into play, because the hacker actually got the password reset by convincing someone he was Mat over the phone. Mat said “Had I used two-factor authentication for my Google account, it’s possible that none of this would have happened”. Similarly, I see passwords compromised all the time by a virus on their local system happily sending credentials off to its owner or creator. The fact is, whether your password is discovered through brute force, social engineering, or another type of hack or compromise, two factor can keep the offender out of your account because with two factor a password just isn’t enough. They only have the thing you know, not the thing you have. And if you lose your phone? Well, then they have the thing you had, but they still need the thing you know. You can even reset your two factor authentication in order to invalidate any keys generated by the lost or stolen device.So, What are the Downsides of Two Factor Authentication?
Let’s get right to it. There are really three things that are required for two factor authentication that are above and beyond what is required for standard username/password authentication. This first two, setting up a two factor app on your device and adding an account to that app, only have to be done once. After that all you need to do is enter a six digit code generated by the app each time you log in.How Do I Get Started?
First, you will need to install and set up a two factor app on your mobile device. You will only have to do this once, no matter how many sites or systems you later set up to use two factor. For this article, I’m using Authy (Android|iPhone), but there are other options such as Google Authenticator (Android|iPhone) as well. I’m using Authy here mostly because it seems to be the most user friendly. When you install Authy, it offers you the option to create an encrypted backup of your codes, which can be useful in the event that you want to move to a new device where applications and their settings don’t automatically transfer.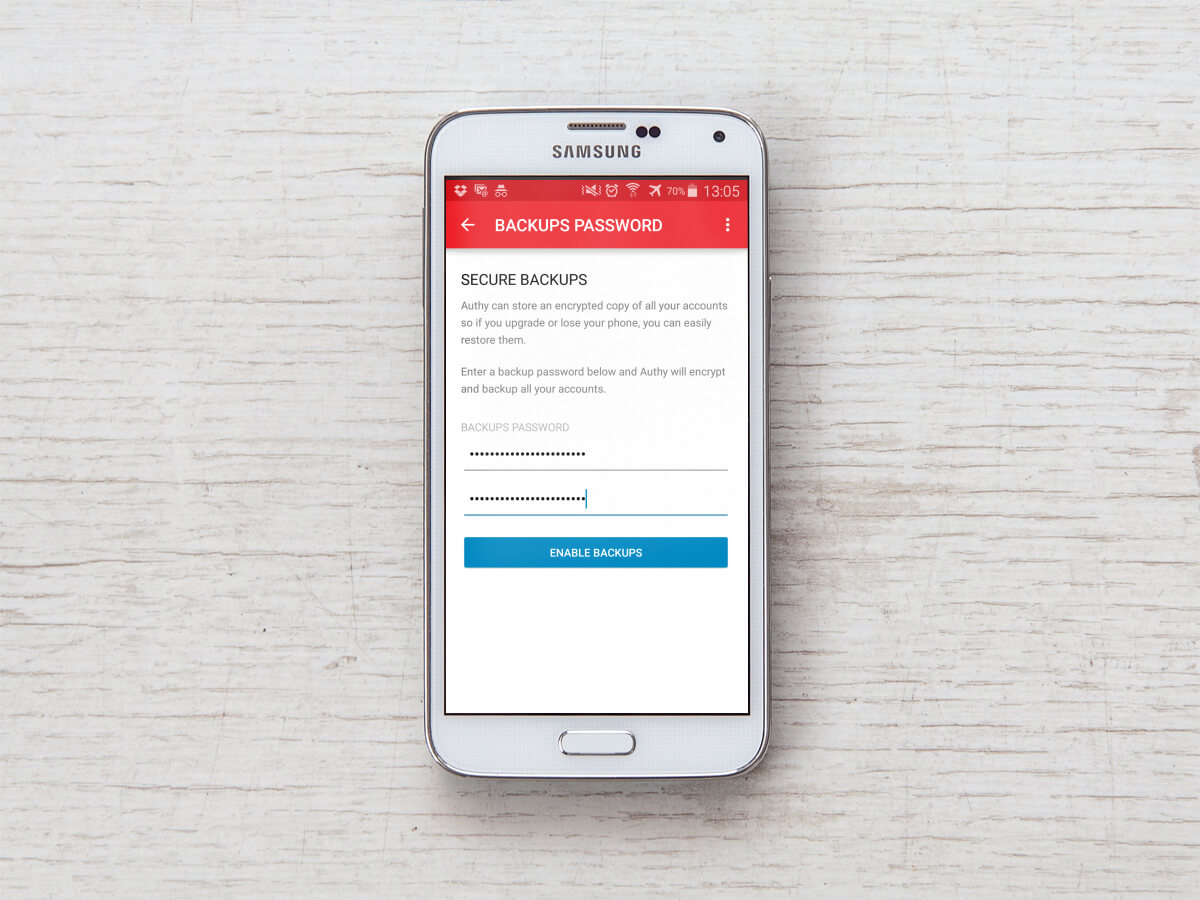 When you add an account, you are given the option to enter a code, or scan a QR code.
When you add an account, you are given the option to enter a code, or scan a QR code.
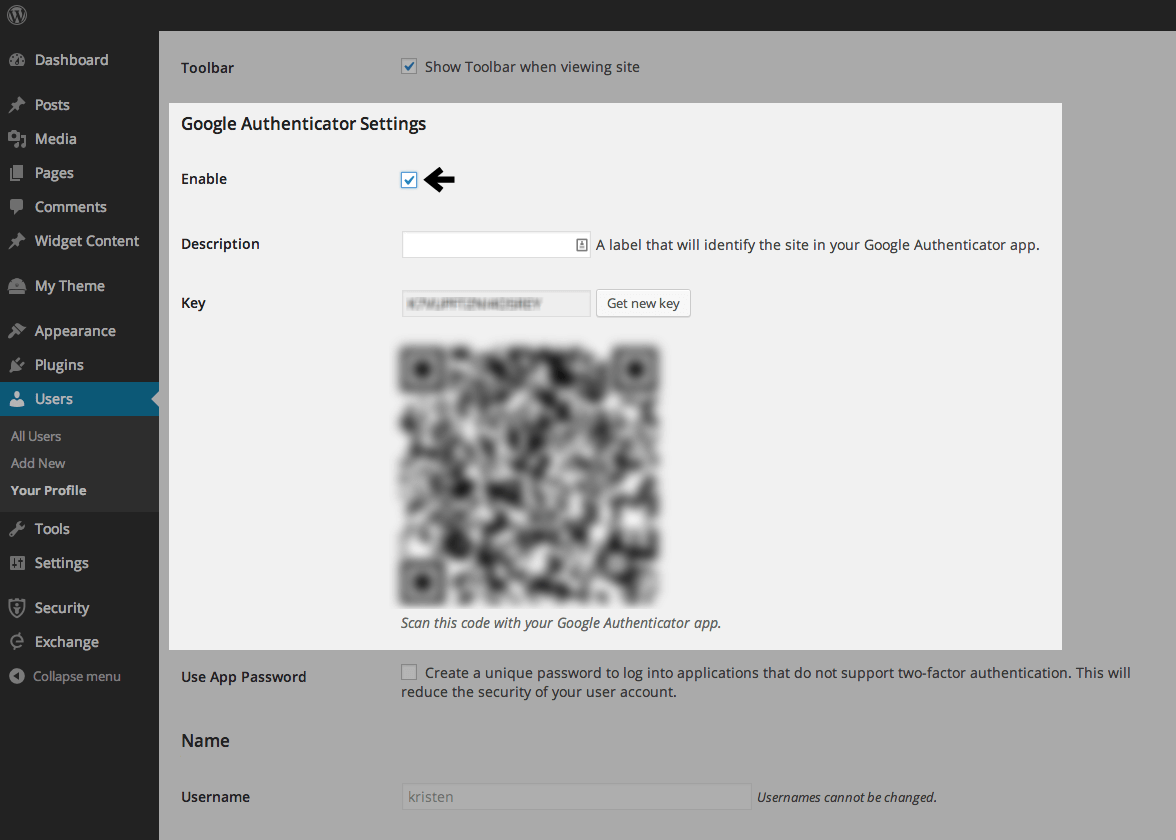
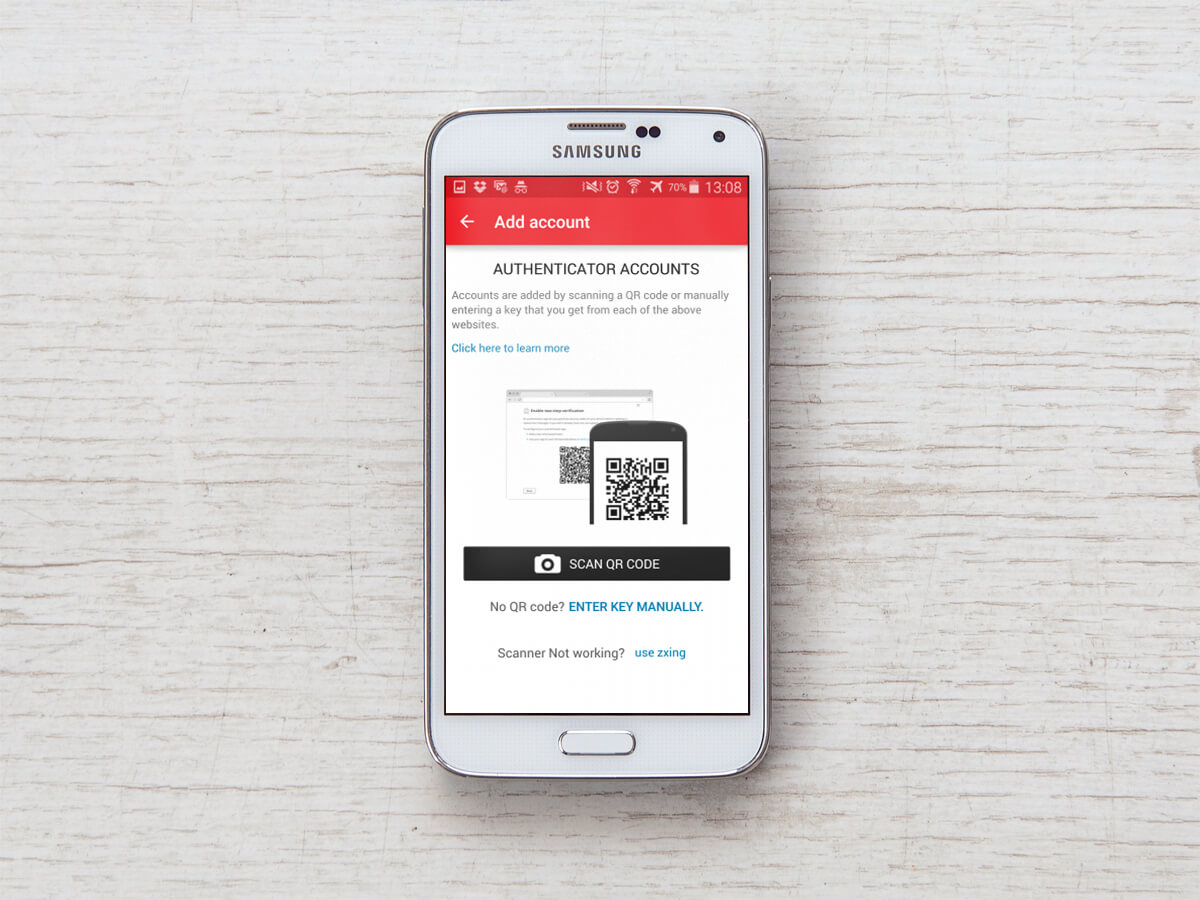 If you choose to scan the QR code, which is generally the simplest option, Authy will use your device’s camera to let you scan a QR code like this one generated by iThemes Security Pro. To find your two factor authentication settings, visit your Profile page in the WordPress dashboard.
If you choose to scan the QR code, which is generally the simplest option, Authy will use your device’s camera to let you scan a QR code like this one generated by iThemes Security Pro. To find your two factor authentication settings, visit your Profile page in the WordPress dashboard.
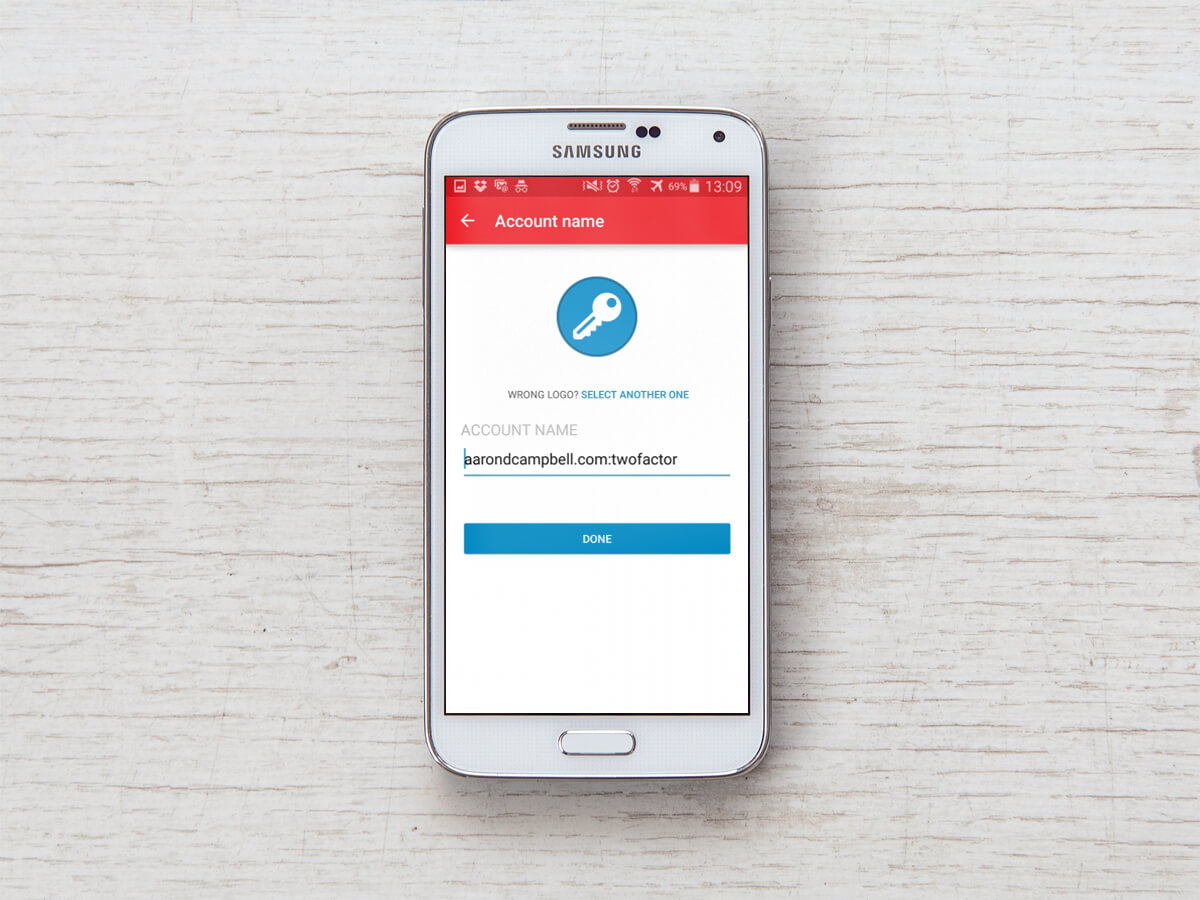
 As soon as Authy recognizes the QR code, it will as you for a name for the account. Name it, click done, and that’s it.
As soon as Authy recognizes the QR code, it will as you for a name for the account. Name it, click done, and that’s it.
 Now when you log in, you will launch Authy and enter the six digit code it gives you. This is the only thing that you will have to do each time you log in, everything before this is “set it and done”.
Now when you log in, you will launch Authy and enter the six digit code it gives you. This is the only thing that you will have to do each time you log in, everything before this is “set it and done”.

Is Two Factor Authentication Worth the Extra Effort?
Yes! Strong passwords are a must, but two factor authentication adds a whole new layer of security that you simply can’t get with only a passwordTwo Factor Authentication FAQs
Q: What if I’m out of cell phone service range, or I’m in a foreign country? A: Neither Authy or Google Authenticator require cell phone service. Q: What do I do if my phone is dead? A: Some services allow you to print out a list of backup codes that you can put in your wallet, but honestly it might just be the time to take a break! Q: What if my phone is lost or stolen? A: This is one of the reasons I chose to use Authy. When you get a new device, set Authy back up and have it restore your backed up accounts. It’s that easy. Q: So I need an app on my phone just to secure my website? A: No! Use that new app on your phone to secure your entire online presence. That same app can be use to do two-factor authentication with GMail, LastPass, DropBox, Basecamp, Amazon Web Services, SiteGround, and many more.More Reading
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed