WordPress Vulnerability Report: May 2021, Part 2
Vulnerable plugins and themes are the #1 reason WordPress websites get hacked. The weekly WordPress Vulnerability Report powered by WPScan covers recent WordPress plugin, theme, and core vulnerabilities, and what to do if you run one of the vulnerable plugins or themes on your website. Each vulnerability includes a severity rating of Low, Medium, High, or Critical.

Vulnerable plugins and themes are the #1 reason WordPress websites get hacked. The weekly WordPress Vulnerability Report powered by WPScan covers recent WordPress plugin, theme, and core vulnerabilities, and what to do if you run one of the vulnerable plugins or themes on your website.
Each vulnerability includes a severity rating of Low, Medium, High, or Critical. Responsible disclosure and reporting of vulnerabilities is an integral part of keeping the WordPress community safe. Please share this post with your friends to help get the word out and make WordPress safer for everyone!
WordPress Core Vulnerabilities
WordPress Plugin Vulnerabilities
1. Simple Admin Language Change

Plugin: Simple Admin Language Change
Vulnerability: Arbitrary User Locale Change
Patched in Version: 2.0.2
Severity Score: 4.3 Medium
2. Ship To Ecourier

Plugin: Ship to eCourier
Vulnerability: Plugin’s Settings Update via CSRF
Patched in Version: 1.0.2
Severity Score: 5.4 Medium
3. Parcel Tracker eCourier

Plugin: Parcel Tracker eCourier
Vulnerability: Plugin’s Settings Update via CSRF
Patched in Version: 1.0.2
Severity Score: 5.4 Medium
4. PickPlugins Product Slider for WooCommerce
Plugin: PickPlugins Product Slider for WooCommerce
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 1.13.22
Severity Score: 7.1 High
5. Hana Flv Player
Plugin: Hana Flv Player
Vulnerability: Authenticated Stored Cross-Site Scripting
Patched in Version: No known fix
Severity Score: 3.8 Low
6. Hotjar Connecticator
Plugin: Hotjar Connecticator
Vulnerability: Authenticated Stored Cross-Site Scripting
Patched in Version: No known fix – plugin closed
Severity Score: 3.8 Low
7. GA Google Analytics

Plugin: GA Google Analytics
Vulnerability: Authenticated Stored Cross-Site Scripting
Patched in Version: No known fix
Severity Score: 5.9 Medium
8. Target First Plugin
Plugin: Target First Plugin
Vulnerability: Unauthenticated Stored Cross-Site Scripting via Licence Key
Patched in Version: 1.0
Severity Score: 7.2 High
9. Leads-5050 Visitor Insights

Plugin: Leads-5050 Visitor Insights
Vulnerability: Unauthorized License Change
Patched in Version: 1.1.0
Severity Score: 7.1 High
10. DSGVO All in one for WP

Plugin: DSGVO All in one for WP
Vulnerability: Unauthenticated Stored Cross-Site Scripting
Patched in Version: 4.0
Severity Score: 8.3 High
11. UltimateWoo
Plugin: UltimateWoo
Vulnerability: PHP Object Injection
Patched in Version: No known fix – plugin closed
Severity Score: 5.6 Medium
12. Ultimate Member

Plugin: Ultimate Member
Vulnerability: Authenticated Reflected Cross-Site Scripting
Patched in Version: 2.1.20
Severity Score: 4.4 Medium
13. Autoptimize

Plugin: Autoptimize
Vulnerability: Authenticated Stored Cross-Site Scripting
Patched in Version: 2.8.4
Severity Score: 6.6 Medium
14. Zlick Paywall

Plugin: Zlick Paywall
Vulnerability: CSRF Bypasses
Patched in Version: 2.2.2
Severity Score: 3.1 Low
15. ThemeHigh WooCommerce Wishlist and Comparison

Plugin: ThemeHigh WooCommerce Wishlist and Comparison
Vulnerability: Unauthorized AJAX call
Patched in Version: 1.0.5
Severity Score: 7.2 High
16. Simple Giveaways
Plugin: Simple Giveaways
Vulnerability: Unauthenticated Reflected Cross-Site Scripting
Patched in Version: 2.36.2
Severity Score: 7.1 High
17. ReDi Restaurant Reservations

Plugin: ReDi Restaurant Reservations
Vulnerability: Unauthenticated Stored Cross-Site Scripting
Patched in Version: 21.0426
Severity Score: 7.1 High
18. All in One SEO Pack
Plugin: All in One SEO Pack
Vulnerability: Remote Code Execution
Patched in Version: 4.1.0.2
Severity Score: 6.6 Medium
19. LifterLMS

Plugin: LifterLMS
Vulnerability: Authenticated Stored Cross-Site Scripting in Edit Profile
Patched in Version: 4.21.1
Severity Score: 7.4 High
Vulnerability: Reflected Cross-Site Scripting via Coupon Code in Checkout
Patched in Version: 4.21.1
SeverityScore: 6.1 Medium
WordPress Theme Vulnerabilities
A Note on Responsible Disclosure
You might be wondering why a vulnerability would be disclosed if it gives hackers an exploit to attack. Well, it is very common for a security researcher to find and privately report the vulnerability to the software developer before it goes public.
With responsible disclosure, the researcher’s initial report is made privately to the developers of the company that owns the software, but with an agreement that the full details will be published once a patch has been made available. For significant security vulnerabilities, there may be a slight delay in disclosing the vulnerability to give more people time to patch.
The security researcher may provide a deadline for the software developer to respond to the report or to provide a patch. If this deadline is not met, then the researcher may publicly disclose the vulnerability to put pressure on the developer to issue a patch.
Publicly disclosing a vulnerability and seemingly introducing a Zero-Day vulnerability–a type of vulnerability that has no patch and is being exploited in the wild– may seem counterproductive. But, it is the only leverage that a researcher has to pressure the developer to patch the vulnerability.
If a hacker were to discover the vulnerability, they could quietly use the Exploit and cause damage to the end-user(this is you), while the software developer remains content on leaving the vulnerability unpatched. Google’s Project Zero has similar guidelines when it comes to disclosing vulnerabilities. They publish the full details of the vulnerability after 90 days whether or not the vulnerability has been patched.
How to Protect Your WordPress Website From Vulnerable Plugins and Themes
There are three great ways to automatically protect your websites from vulnerable themes and plugins:
- Enabling Auto-Updates for Plugins and Themes
- The iThemes Security Pro plugin’s Site Scanner
- Version Management in iThemes Security
1. Enable Auto-Updates for Plugins and Themes
Starting in WordPress 5.5, you can enable auto-updates for plugins and themes. Why would auto-updates be rolled into WordPress core? Outdated plugins and themes are still the #1 reason WordPress sites get hacked. Version releases often include important security patches to close vulnerabilities (just check out how many security issues with themes and plugins are disclosed from month to month in our WordPress vulnerability roundup). That’s why always running the latest version of any plugin or theme you have installed on your site is a security best practice.
Now WordPress core will allow you to set plugins and themes to update automatically from your WordPress admin > Plugins > Installed Plugins and Appearance > Themes pages. This way, you can always know your site is running the latest code available.
2. Activate the iThemes Security Pro Plugin’s Site Scanner
The iThemes Security Pro plugin’s Site Scanner is another way to secure and protect your WordPress website from the number one cause of all software hacks: outdated plugins and themes with known vulnerabilities. The Site Scanner checks your site for known vulnerabilities and automatically applies a patch if one is available.
The 3 Types of WordPress Vulnerabilities Checked by the iThemes Security Pro Site Scanner:
- WordPress Core Vulnerabilities
- Plugin Vulnerabilities
- Theme Vulnerabilities
To enable the Site Scan on your site, navigate to the iThemes Security Pro settings and click the Enable button on the Site Scan settings module.
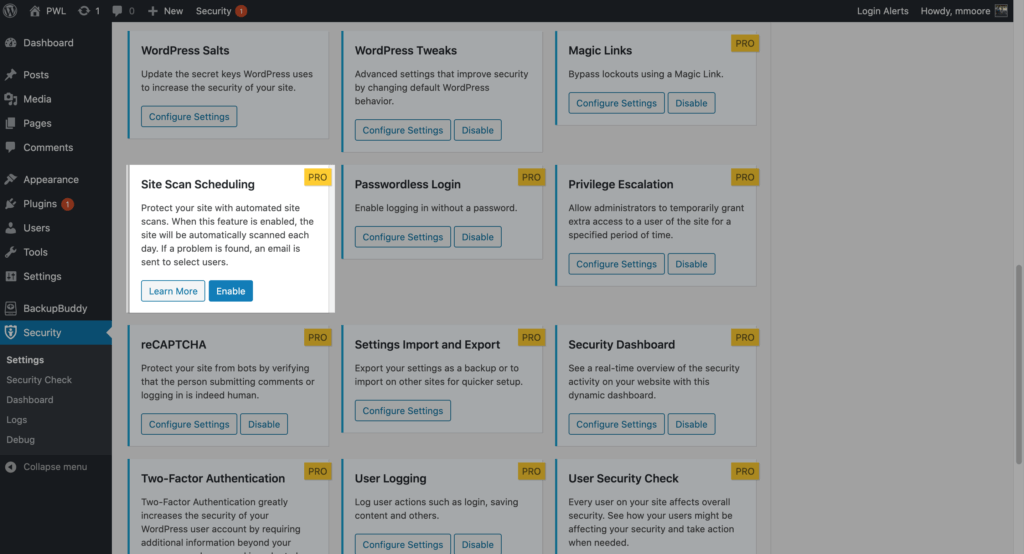
To trigger a manual Site Scan, click the Scan Now button on the Site Scan Widget located on the right side-bar of the security settings.
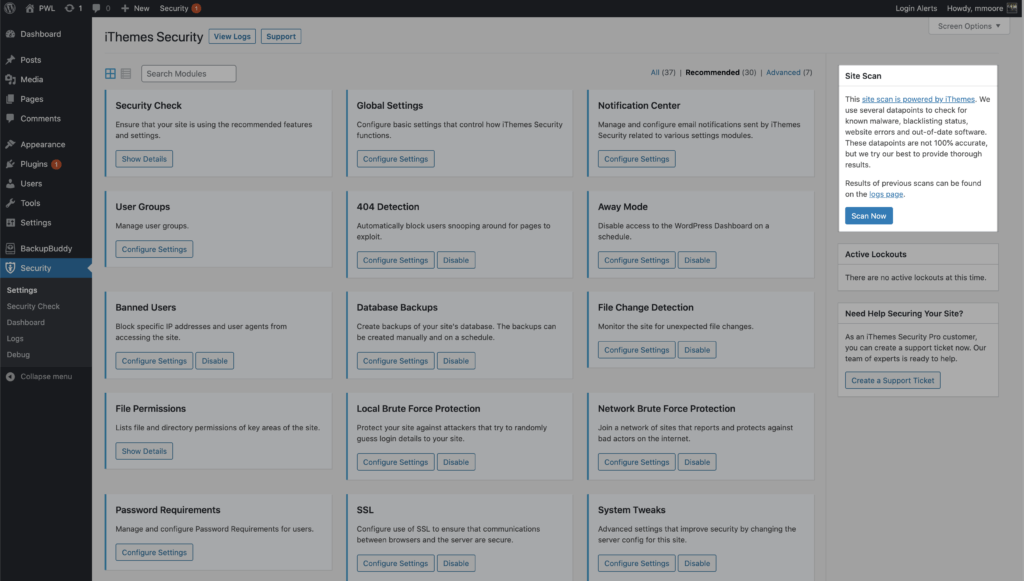
The Site Scan results will display in the widget.
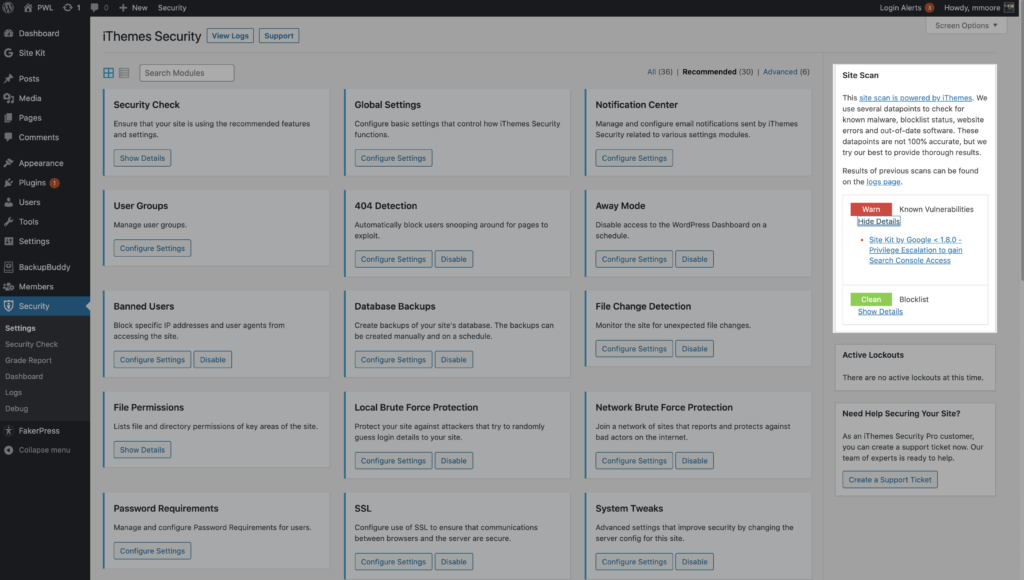
If the Site Scan detects a vulnerability, click the vulnerability link to view the details page.
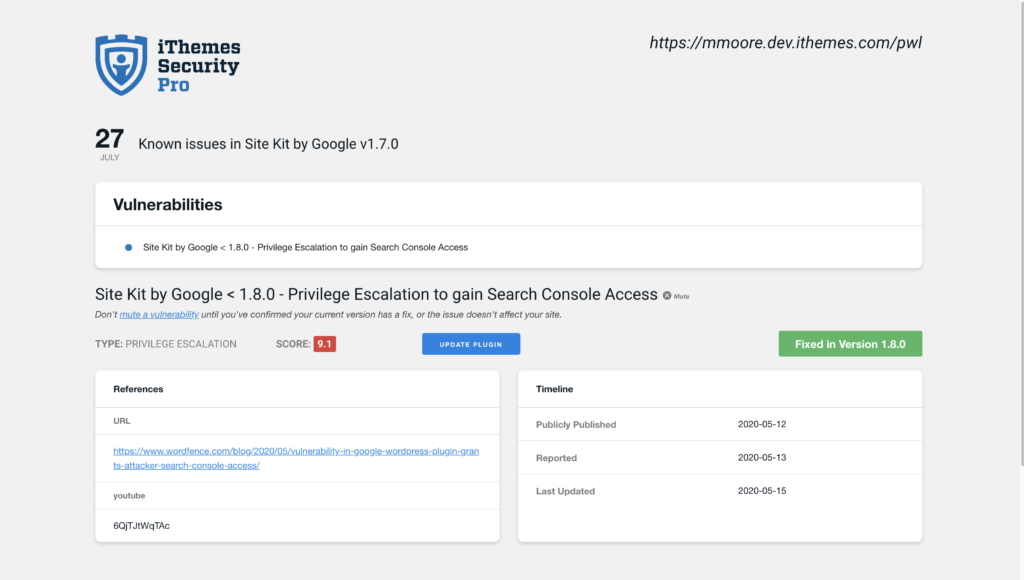
On the Site Scan vulnerability page, you will see if there is a fix available for the vulnerability. If there is a patch available, you can click the Update Plugin button to apply the fix on your website.
There can be a delay between when a patch is available and the iThemes Security Vulnerability Database getting updated to reflect the fix. In this case, you can mute the notification to not receive any more alerts related to the vulnerability.
3. Enable Version Management in iThemes Security Pro
iThemes Security Pro’s Version Management feature allows you to have a bit more control over auto-updates for WordPress, plugins, and themes.
Here are the three ways iThemes Security Pro Version Management offers more flexibility compared to the default WordPress auto-updates.
- Streamlined plugin and theme management – manage all of your plugin and theme updates from the version management settings.
- Add custom delay periods for plugin and theme updates – WordPress auto-updates only offers the option to apply updates immediately. The update scheduler allows you to create a custom delay. Delaying can be a good option for plugins or themes that tend to need some follow-up releases to fix issues after a major release.
- Only Apply Updates that Fix Known Vulnerabilities – only apply updates that fix known vulnerabilities. This option is perfect if you like to manually run all of your updates but want to receive security patches immediately.
Beyond that, Version Management also has options to harden your website when you are running outdated software and scan for old websites.
To get started using Version Management, enable the module on the main page of the security settings.
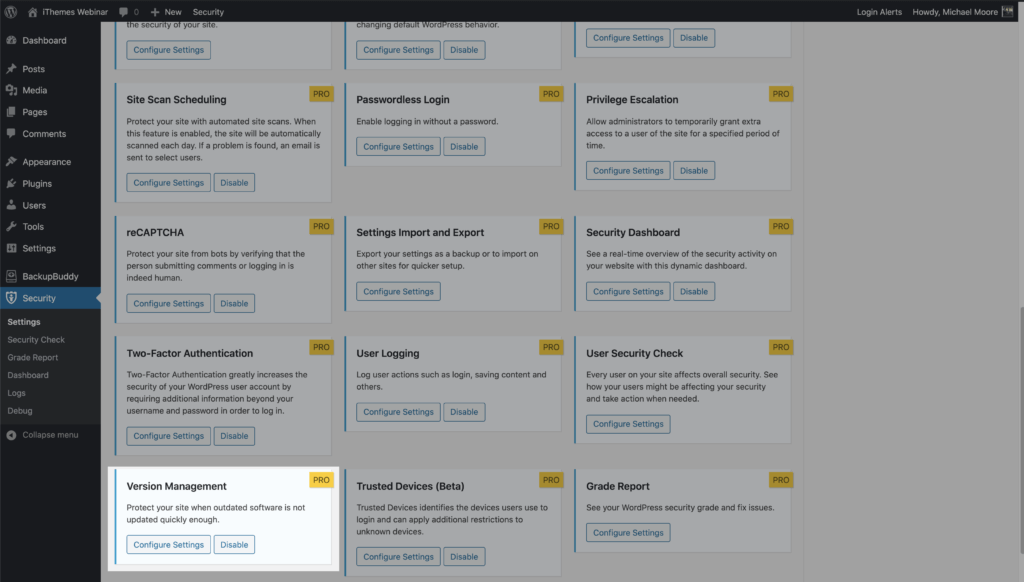
Now click the Configure Settings button to take a closer look at the settings.
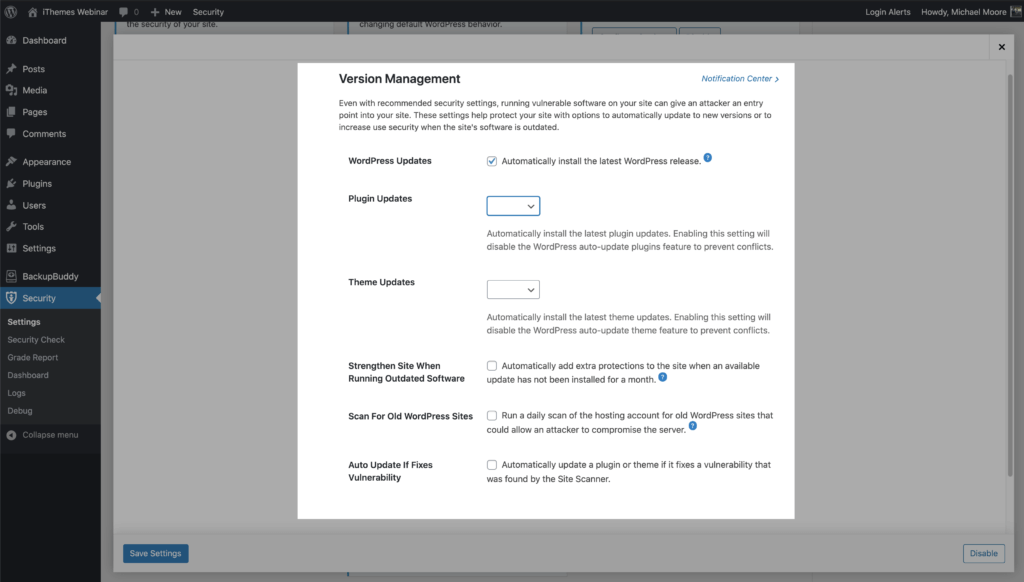
- WordPress Updates – Automatically install the latest WordPress release.
- Plugin Updates – Automatically install the latest plugin updates. Enabling this setting will disable the WordPress auto-update plugins feature to prevent conflicts.
- Theme Updates – Automatically install the latest theme updates. Enabling this setting will disable the WordPress auto-update theme feature to prevent conflicts.
- Strengthen Site When Running Outdated Software – Automatically add extra protections to the site when an available update has not been installed for a month.
- Force all users that do not have two-factor enabled to provide a login code sent to their email address before logging back in.
- Disable the WP File Editor (which blocks people from editing plugin or theme code).
- Disable XML-RPC pingbacks, and block multiple authentication attempts per XML-RPC request (both of which will make XML-RPC stronger against attacks without having to turn it off completely).
- Scan For Old WordPress Sites – Run a daily scan of the hosting account for old WordPress sites that could allow an attacker to compromise the server. A single outdated WordPress site with a vulnerability could allow attackers to compromise all the other sites on the same hosting account.
- Auto Update If Fixes Vulnerability – This option works in tandem with the iThemes Security Pro Site Scan to check your website for known WordPress, plugin, and theme vulnerabilities and apply a patch when one is available.
Now let’s take a closer look at configuring plugin and theme updates. Before we get started, I wanted to give a quick reminder that enabling the plugin and theme update settings will disable the WordPress auto-update feature to prevent conflicts.
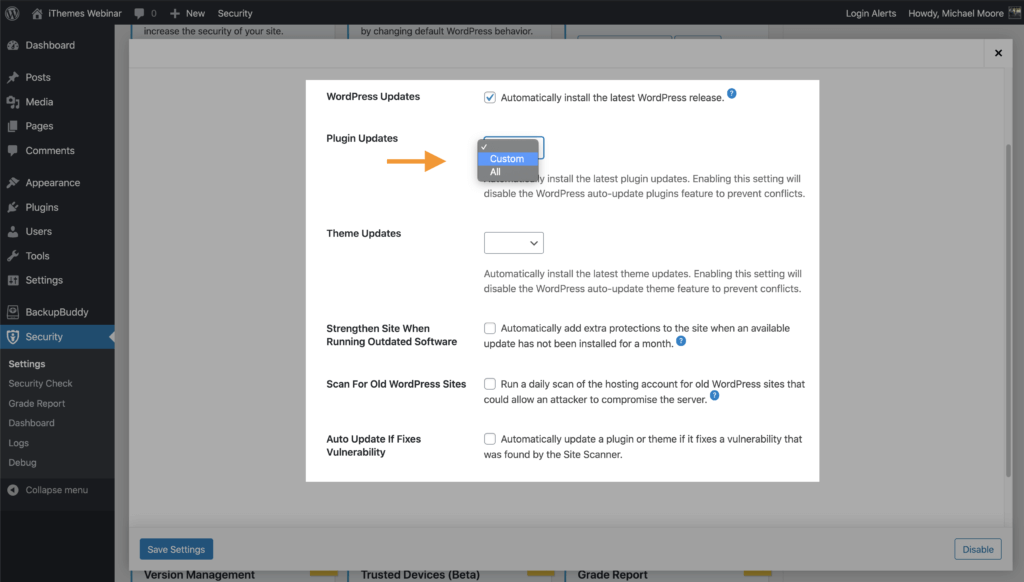
Both the Plugin and Theme Update Settings have three choices.
- Blank/None – Leaving the setting blank will allow WordPress to manage the plugin and theme updates.
- Custom – The Custom option allows you to customize the updates precisely to your liking. We will cover this more in just a bit.
- All – All will update all your plugins or themes as soon as an update is available.
Now let’s take a closer look at the Custom option.
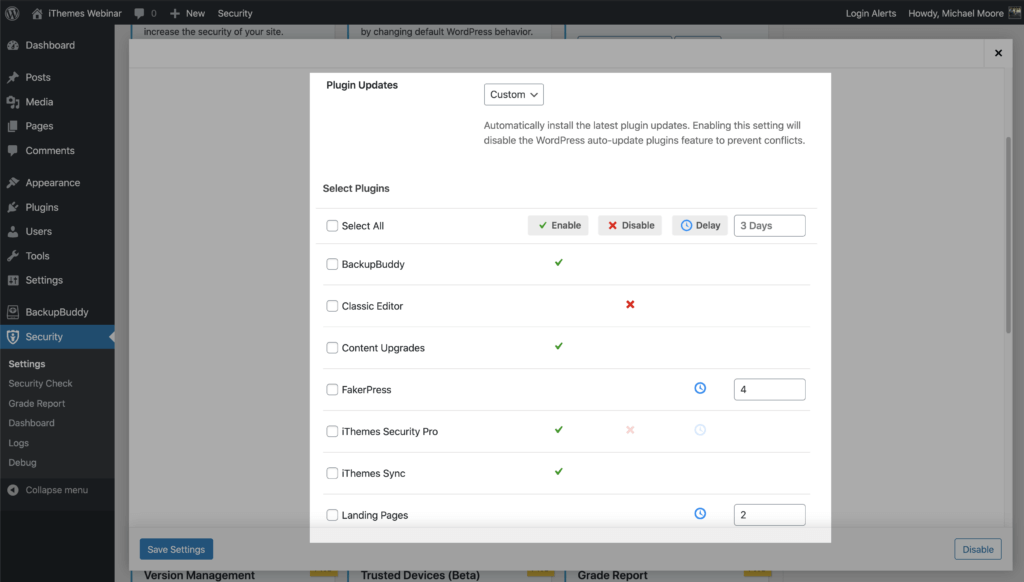
Selecting the Custom option provides three different choices for your plugin and theme updates.
- Enable – Choose which plugins you want to update immediately after a new release.
- Disable – Use this option for plugins that you want to update manually.
- Delay – The delay option allows you to set the number of days you want to delay an update of a release. This can be a good option for developers that tend to need some follow up releases to fix issues after a major release.
Get iThemes Security Pro Today
iThemes Security Pro, our WordPress security plugin, offers 50+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add an extra layer of security to your website.
Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed