WordPress Vulnerability Roundup: March 2021, Part 2
New WordPress plugin and theme vulnerabilities were disclosed during the third week of March. This report covers recent WordPress plugin, theme, and core vulnerabilities and what to do if you run one of the vulnerable plugins or themes on your website. The WordPress Vulnerability Roundup is divided into three different categories: WordPress core, WordPress plugins, and WordPress themes.

New WordPress plugin and theme vulnerabilities were disclosed during the third week of March. This report covers recent WordPress plugin, theme, and core vulnerabilities and what to do if you run one of the vulnerable plugins or themes on your website.
The WordPress Vulnerability Roundup is divided into three different categories: WordPress core, WordPress plugins, and WordPress themes.
Each vulnerability will have a severity rating of Low, Medium, High, or Critical. The severity ratings are based on the Common Vulnerability Scoring System.
WordPress Core Vulnerabilities
WordPress 5.7 “Esperanza” Released – Update Now!
A new WordPress core version was released on March 9, 2021: WordPress 5.7 “Esperanza.”
Be sure to update all your sites to this latest version of WordPress. Check out 21 new features and enhancements in WordPress 5.7 to see what’s new, including:
- An easier way to send password reset emails/links
- Upgrade a site from HTTP to HTTPS with a single click
- Custom icon and background colors + sizes for social icons block
WordPress Plugin Vulnerabilities
1. Advanced Order Export For WooCommerce

Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 3.1.8
Severity: High: CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:H/I:H/A:L
2. User Profile Picture
Vulnerability: Sensitive Information Disclosure
Patched in Version: 2.5.0
Severity: Medium: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N
3. Database Backups
Vulnerability: CSRF to Backup Download
Patched in Version: No Known Fix – Plugin Closed
Severity: High: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:N/A:N
4. The Plus Addons for Elementor Page Builder (Premium Version)
Vulnerability: Authentication Bypass
Patched in Version: 4.1.7 (Actively Being Exploited Update Now)
Severity: Critical: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
5. Super Interactive Maps
Vulnerability: Unauthenticated SQL Injections
Patched in Version: 2.2
Severity: Critical: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:L
6. SuperStoreFinder
Vulnerability: Unauthenticated SQL Injections
Patched in Version: 6.5
Severity: Critical: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:L
7. Five Star Restaurant Menu
Vulnerability: Unauthenticated PHP Object Injection
Patched in Version: 2.2.1
Severity: High: CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:L
8. JH 404 Logger
Vulnerability: Unauthenticated Stored Cross-Site Scripting
Patched in Version: No Known Fix – Plugin Closed
Severity: Critical: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
9. WP File Manager
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 7.1
Severity: Medium – CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:C/C:L/I:L/A:L
10. VM Backups
Vulnerability: CSRF to Database Backup Download
Patched in Version: No Known Fix – Plugin Closed
Severity: Medium: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N
11. Related Posts for WordPress

Vulnerability: Authenticated Reflected Cross-Site Scripting
Patched in Version: 2.0.4
Severity: Medium: CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N
WordPress Theme Vulnerabilities
March Security Tip: Use Two-Factor Authentication to Secure
Using two-factor authentication for your WordPress website user logins can help keep your website secure even if you use one of the plugins in this edition of the vulnerability roundup with an authentication bypass vulnerability.
Using two-factor authentication for your WordPress website user logins can help keep your website secure even if you are using a plugin with an authentication bypass vulnerability.
Why? Two-factor authentication makes it nearly impossible for an unauthenticated user to login to your website.
What is two-factor authentication? Two-factor authentication is a process of verifying a person’s identity by requiring two separate methods of verification. Two-factor authentication adds an extra layer of WordPress security to verify it’s actually you logging in and not someone who gained access (or even guessed) your password.
Here are a few more reasons to use two-factor authentication to add another layer of protection to your WordPress login.
- Reused passwords are weak passwords. According to the Verizon Data Breach Investigations Report, over 70% of employees reuse passwords at work. But the most important stat from the report is that “81% of hacking-related breaches leveraged either stolen or weak passwords.”
- Even though 91% of people know reusing passwords is poor practice, a staggering 59% of people still reuse their passwords everywhere!
- Many people are still using passwords that have appeared in a database dump. A database dump occurs when a hacker successfully gains access to a user database and then dumps the contents somewhere online. Unfortunately for us, these dumps contain a ton of sensitive login and account information.
- The “Collection #1″ Data Breach that was hosted on MEGA hosted included 1,160,253,228 unique combinations of email addresses and passwords. This kind of score will provide a malicious bot with over a billion sets of credentials to use in brute force attacks. A brute force attacks refer to a trial and error method used to discover username and password combinations to hack into a website.
- Even if you have a strong password, you’re only as secure as every other admin user on your site. Okay, so you are the type of person that uses a password manager like LastPass to create strong and unique passwords for each of your accounts. But what about the other administrator and editor users on your site? If an attacker was able to compromise one of their accounts, they could still do a ton of damage to your website.
- Google has said two-factor authentication is effective against 100% of automated bot attacks. That alone is a pretty good reason.
How to Add Two-Factor Authentication to Secure Your WordPress Login with iThemes Security Pro
The iThemes Security Pro plugin makes it easy to add two-factor authentication to your WordPress websites. With iThemes Security Pro’s WordPress two-factor authentication, users are required to enter both a password AND a secondary code sent to a mobile device such as a smartphone or tablet. Both the password and the code are required to successfully log in to a user account.
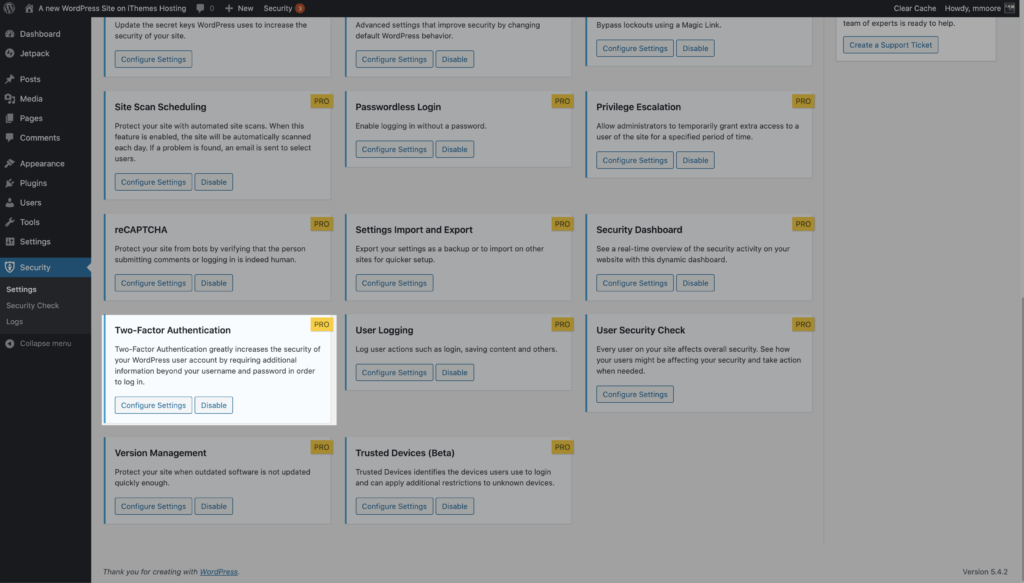
To start using Two-Factor Authentication on your website, enable the feature on the main page of the iThemes Security Pro settings.
In this post, we unpack all the steps of how to add two-factor authentication to your site with iThemes Security Pro, including how to use a third-party app like Google Authenticator or Authy.
See how it works
WordPress Disaster Week Starts Today! Live Webinars March 16 – 18, 2021
Are you ready if disaster strikes your WordPress website today? From running an update that breaks everything to hacks or accidentally deleting an important file, the reality is it’s not a matter of if but when something will go wrong with your site. And now, more than ever, the security threats your website faces are very real.
To help you combat the threat of website disasters, we’re hosting the biggest free, online iThemes training event of the year so that EVERYONE can have a plan if and when a website catastrophe strikes.
Grab your spot here for WordPress Disaster Week, happening March 16, 17 & 18, 2021, with daily sessions happening from 1:00 – 3:00 p.m. (CT).
During this training, we’ll cover a complete plan for how to prevent and recover when website calamity strikes, including:
- How to defend your site from the most common types of attacks in 2021
- Signs you’ve been hacked
- How to restore your site from a backup when something goes wrong
- How to strengthen your site’s security with the iThemes Security Plugin
- How to make money selling website backup & security services to clients
Can’t make the live training time? Go ahead and register and we’ll email you the video replays to watch at your convenience. See webinar time in your time zone here
Register now
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed